Being able to access a system without remembering 1000 different passwords all the time is really convenient and at least saves me a lot of time.
SSH (Secure Shell) provides a way of doing this by using private and public keys where the private key is something you should keep for yourself and the public key is distributed to the target systems.
You have two options here:
- Configure your private key with a password meaning you type same password all the time when accessing remote systems.
- If you’re lazy or would like to e.g. run remote scripts without password prompt and do not want to give a password at all you configure your private key without a password.
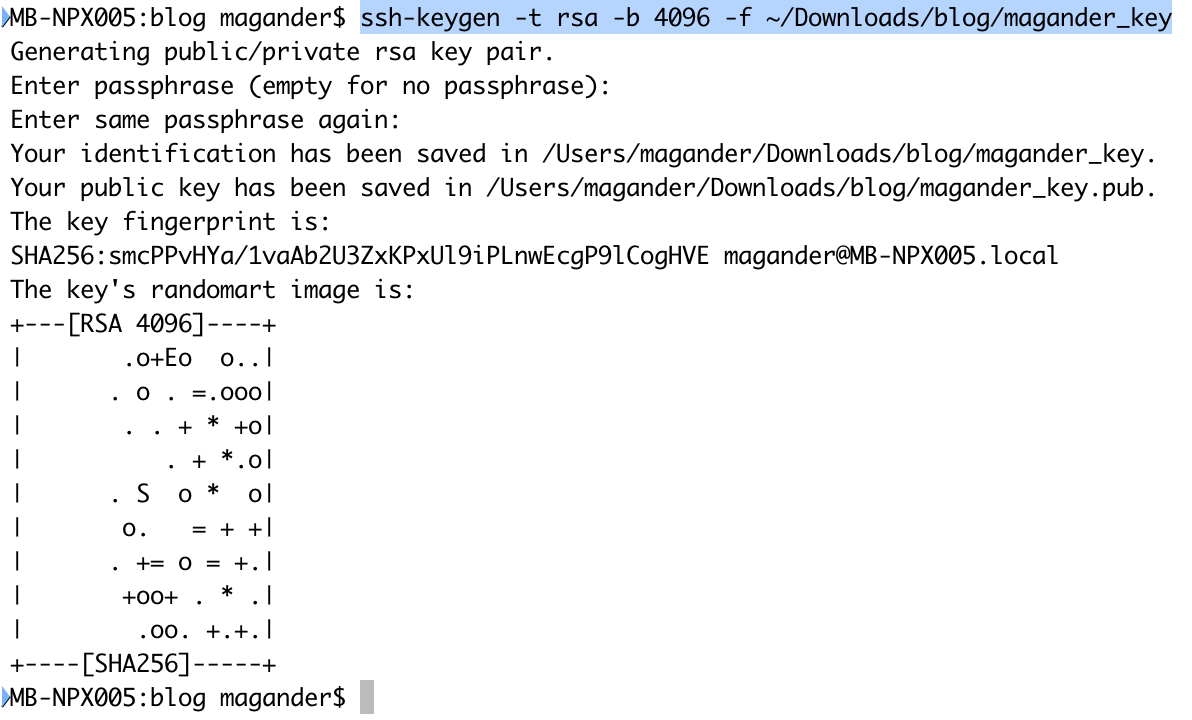
In the below example I’ll take the lazy route by creating the SSH keys without a passphrase meaning I do not have to provide a password when logging into remote systems.
- Use ssh-keygen to generate your private and public key. the key generator will save the files to a directory called .ssh in your home directory but since I would like to place the files in another directory I’ll use the -f option. I’m not providing a password when running the ssh-keygen command.
- Verify you got two files in the directory. I’ll have:
- magander_key – Your very very secret private key which you keep to yourself and yourself only. The private key is called id_rsa unless you provide a file name during the key generation process.
- magander_key.pub – This is the public key which is called id_rsa.pub unless you provide a file name during the key generation process.

- Set appropriate permission on the SSH key files:
- chmod 600 ~/Downloads/blog/magander_key
- chmod 644~/Downloads/blog/magander_key.pub
- Prepare the target machine by:
- Creating a .ssh directory in the users home directory unless there is a directory called .ssh already.
- mkdir ~/.ssh
- Set appropriate permission for the .ssh directory
- chmod 700 ~/.ssh
- Add the content of your public key (magander_key.pub) to the remote system authorized_keys file which is placed in the remote system .ssh directory. In my case there was no authorised_keys file present so I just copied my public key file over and gave it the name authorized_keys
- scp magander_key.pub magander@192.168.10.49:/home/magander/.ssh/authorized_keys
- Set appropriate permissions for the authorized_keys file
- chmod 644 ~/.ssh/authorized_keys
- Creating a .ssh directory in the users home directory unless there is a directory called .ssh already.
That’s it, now you can access your target machine using SSH key files without providing a password when loggin in.
In the below example I’m accessing monitoring-vm-01 using the following command: