A question I have received a few times is if AHV supports promiscuous mode or not.
The easy answer is YES it does.
However there is a huge difference in how promiscuous mode works for AHV compared to another well known hypervisor VMware ESXi.
AHV uses Open vSwitch for network communication in most cases, there is also a regular Linux bridge involved but let’s put that aside for the sake of this discussion.
Open vSwitch acts as a layer-2 learning switch/like a physical switch meaning that it learns the MAC addresses on a particular port by watching the source address of packets coming into the switch via that specific port.
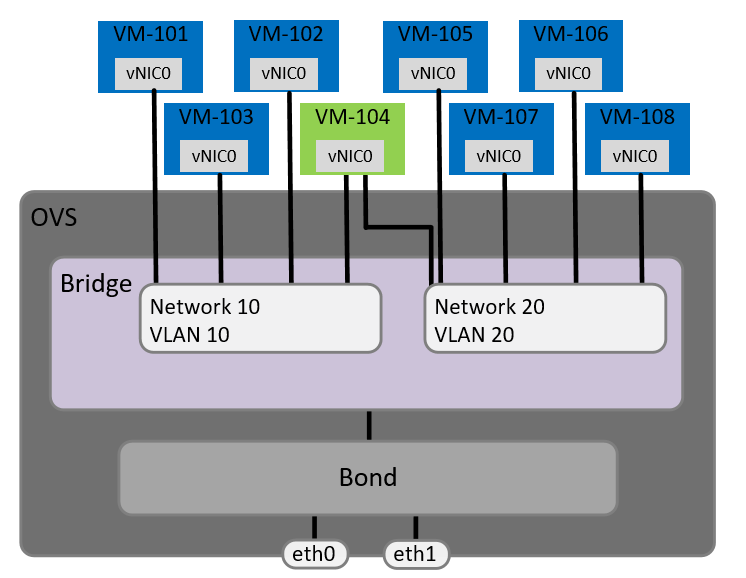
If you put a VM, in this case VM-104, vNIC in promiscuous mode it can see other traffic on the network apart from the network meant for its specific vNIC.
More specifically it, VM-104, can now see traffic meant for VM-104 and also see BUM traffic types meaning:
- Broadcast
- Multicast
- Unknown Unicast – A unicast packet sent to all switch ports by the physical switch since the destination is unknown to the switch
Depending on operating system running inside the VM there are different ways to enable promiscuous mode. The below example covers how to do it for CentOS 7.4.
- Verify if promiscuous mode is turned on or not for eth0 by running:
- ip link show:

- Enable promiscuous mode for eth0 by running:
- ip link set ethX promisc on
- Now verify, check for , if promiscuous mode is enabled or not by running:
- ip link show

If you need to see BUM traffic on more than one AHV network you neet to either add multiple vNICs to a VM or running an acli command to give the VM access to multiple networks shown in the below figure.
The following acli command is used to accoplish this:
vm.nic_update <VM-name> <VM-NIC-MAC-Address> update_vlan_trunk_info=true vlan_mode=kTrunked trunked_networks=<network-1>,<network-2>
In my case i ran the following command to enable VM-104 to see BUM trffic on network demo3000 and demo4000:
vm.nic_update VM-104 52:54:00:42:34:ab update_vlan_trunk_info=true vlan_mode=kTrunked trunked_networks=3000,4000
The 3000 and 4000 values are the network identifiers you get from the command “acli net.list”
Before the change the acli vm.get vm-104 nic_list output section looked like:
nic_list {
ip_address: “192.168.20.28”
mac_addr: “52:54:00:42:34:ab”
network_name: “demo3000”
network_uuid: “bddb769c-7898-4c13-b974-122290e4a82e”
type: “kNormalNic”
uuid: “2517d9ce-d7dd-4e9d-1912-2abc54c12a2a”
vlan_mode: “kAccess”
After the change the same command shows two “trunked_networks” and a change of vlan_mode
nic_list {
ip_address: “192.168.20.128”
mac_addr: “52:54:00:42:34:ab”
network_name: “demo3000”
network_uuid: “bddb769c-7898-4c13-b974-122290e4a82e”
trunked_networks: 3000
trunked_networks: 4000
type: “kNormalNic”
uuid: “2517d9ce-d7dd-4e9d-1912-2abc54c12a2a”
vlan_mode: “kTrunked”
VMware ESXi will show the VM all traffic, and not just BUM traffic, flowing in the port group if you set promiscous mode to Accept. If you need the same behaviour with AHV you need to take advantage of the AHV built-in Network Function Chaining and Service Insertion functionality. This will give you an opportunity to plugin an IDS VM into the OVS Bridge Chain and by that capture and analyse VM-VM traffic within the AHV Host.
The below figure (created by my colleague Jason Burns) illustrates this during a VM A to VM B communication scenario.
Traffic between VMs, in the above figure VM A to VM B (on the same AHV host) leaves VM A and flows from left (br0.local) to right (br0) to left (br0.local) before it reaches VM B. This makes it possible for the IDS VM to see and analyse the traffic. The OVS Bridge Chain is built in to the OVS on each AHV host.
Hope this explains how promiscuous mode and AHV works and in addition also gives you an idea of what is needed to truly achieve/enable OVS switch port mirroring.




2 pings